
jdsingh hacker tool kit a massive hacking tool. Easy tool to generate backdoor This tool compiles a malware with popular payload and then the compiled malware can be execute on windows, android, mac . The malware that created with this tool also have an ability to bypass most antivirus software. || hackers toolkit
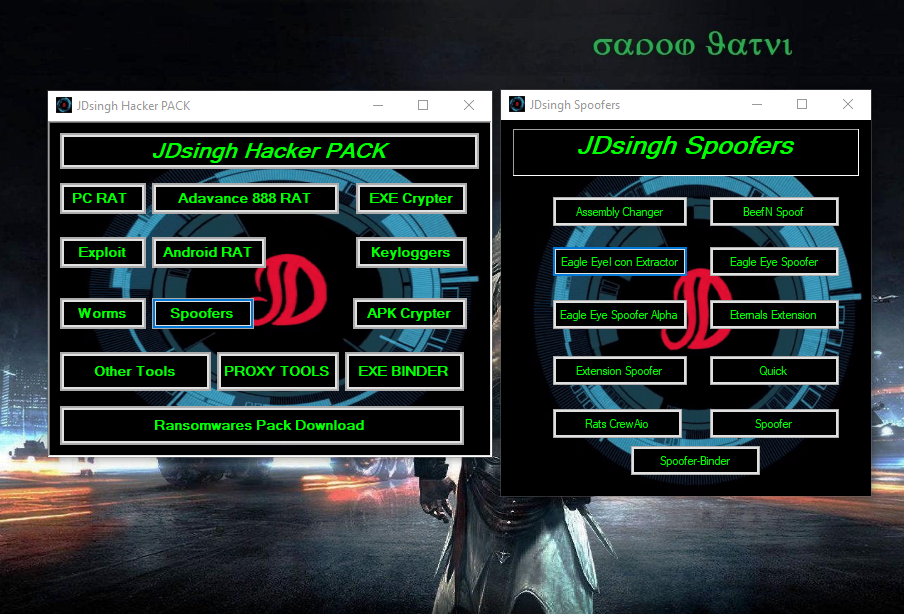
Jdsingh hacker tools
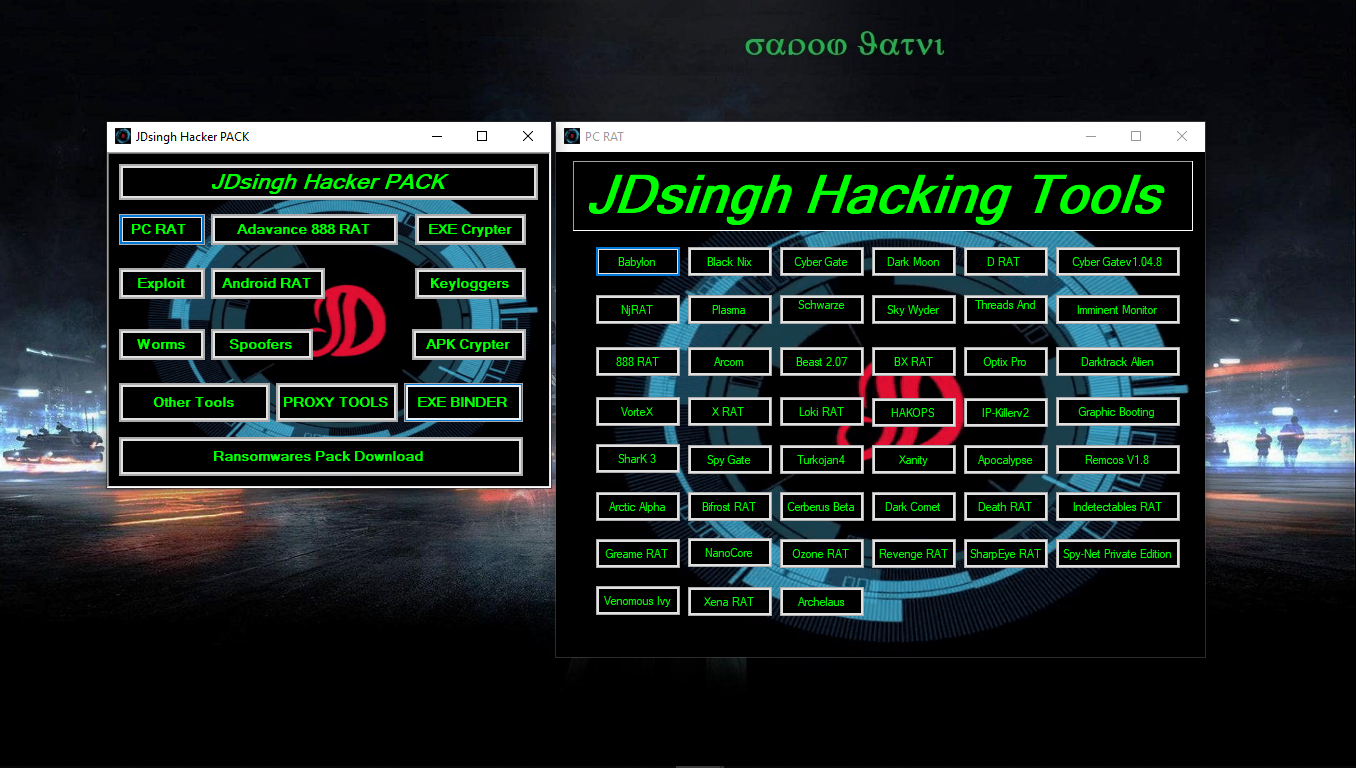
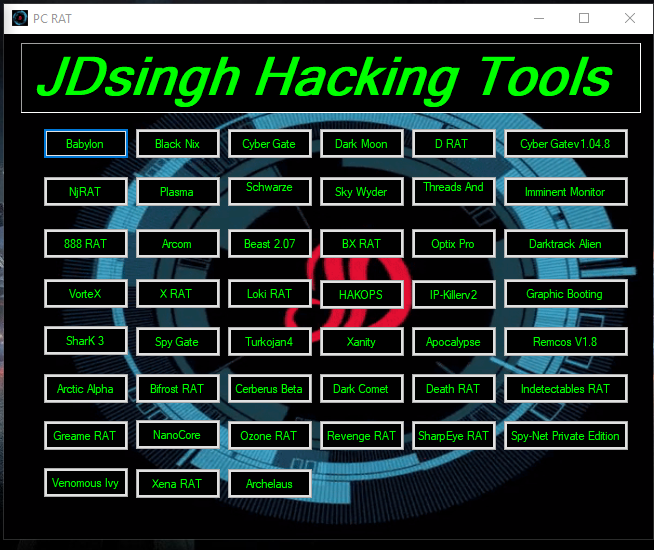
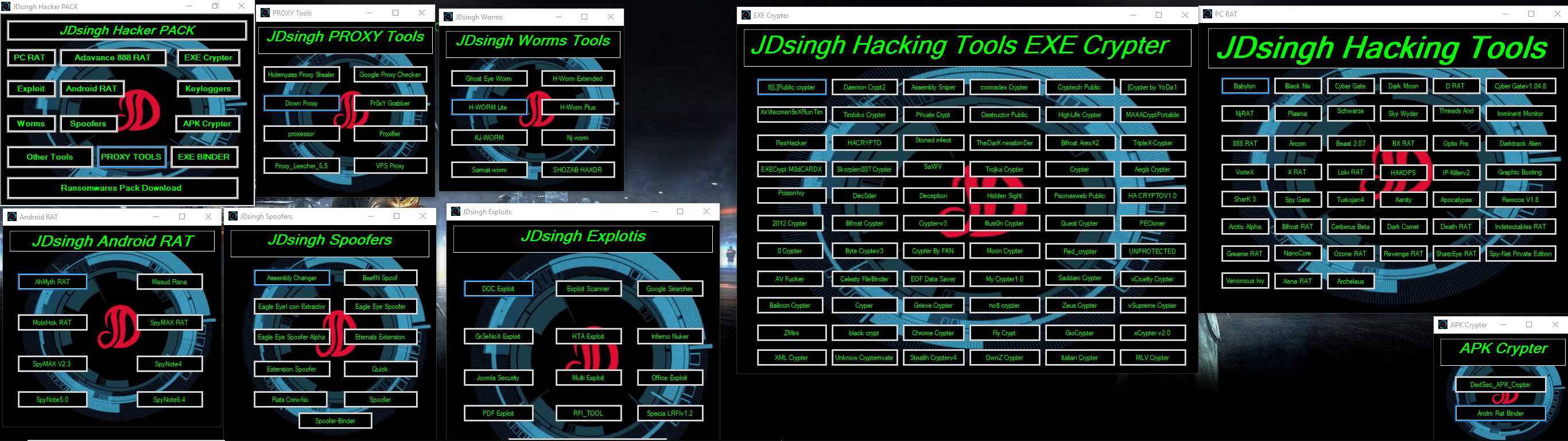
1. computer RATs Tools
2. Adavance 888 RAT
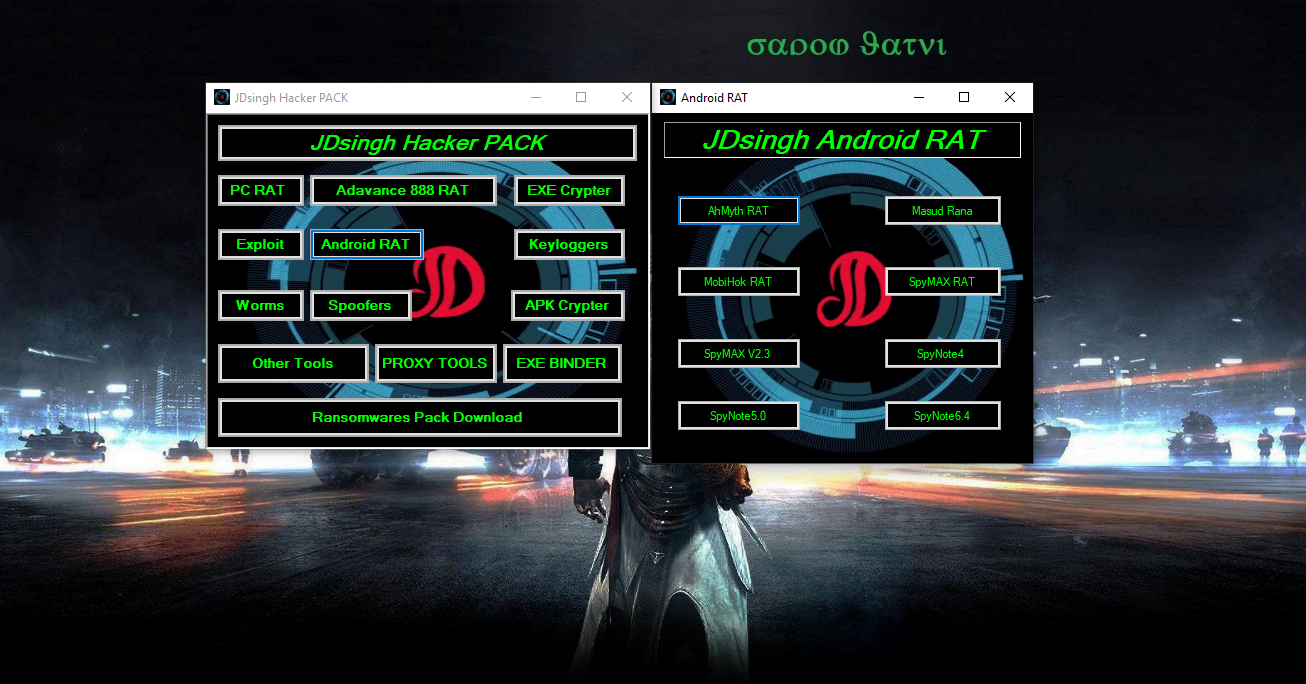
3. Android RAT Tools
4. EXE File Crypter Tools
5. Exploits Tools
6. Keyloggers and password stealers Tools
7. Worms tools kit
8. APK File crypter and Binders Tools
9. File Extension Spoofers Tools
10. Proxy Tools
11. EXE File Binders Tools
12. Others Tools
13. Ransomwares Pack Downloader Tools
1.computer RATs Tools :-
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program — such as a game — or sent as an email attachment. Once the host system is compromised, the intruder may use it to distribute RATs to other vulnerable computers.
40 Plus computers RAT Tools are available in this hacking kit. the available All RAT tools are private stable and prime tools.
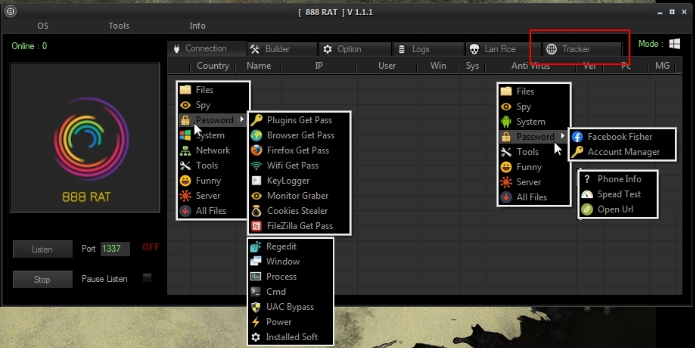
2. Adavance 888 RAT :-
888 RAT is the most powerful Remote Administration Tool. It is the father of all remote administration tools.
888 RAT 1.1.1 Supports both OS Android + Windows. It generates Fully Undetectable Paylod for both android and windows. This version has many new features that are not seen in 888 RAT 1.1.0 version. 888 RAT is a paid tool that costs very expensive. || hackers toolkit
3. Android RAT Tools :-
An android remote administration tool (RAT) is a programmed tool that allows a remote device to control a smartphone as if they have physical access to that system. While screen sharing and remote administration have many legal uses, “RAT” software is usually associated with unauthorized or malicious activity. 8 prime spy RAT are available.
4. EXE File Crypter Tools :-
A crypter is a type of software that can encrypt, obfuscate, and manipulate malware, to make it harder to detect by security programs. It is used by cybercriminals to create malware that can bypass security programs by presenting itself as a harmless program until it gets installed.
5. Exploits Tools
An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in an application or a system to cause unintended or unanticipated behavior to occur. The name comes from the English verb to exploit, meaning “to use something to one’s own advantage”. Basically, this means that the target of an attack suffers from a design flaw that allows people to create the means to access it and use it in his interest.
The zero-day vulnerabilities are by far the most dangerous, as they occur when a software contains a critical security vulnerability of which the vendor is unaware. The vulnerability only becomes known when a hacker is detected exploiting the vulnerability, hence the term zero-day exploit. Once such an exploit occurs, systems running the software are left vulnerable to an attack until the vendor releases a patch to correct the vulnerability and the patch is applied to the software. (PDF Exploit,DOC Exploit, MultiExploit builder,Office Exploit, etc. )
6. Keyloggers and password stealers Tools
Its most basic definition, a keylogger is a function which records or keystrokes on a computer. Taken at this basic level, a keylogger looks absolutely harmless. In the hands of a hacker or a cybercriminal, a keylogger is a potent tool to steal away your information. In This tool kit a 20 Plus Keyloggers and password stealers Tools are available.
7. Worms tools kit
A computer worm is a type of malware that spreads copies of itself from computer to computer. A worm can replicate itself without any human interaction, and it does not need to attach itself to a software program in order to cause damage. || hackers toolkit
They spread over computer networks by exploiting operating system vulnerabilities. Worms typically cause harm to their host networks by consuming bandwidth and overloading web servers. Computer worms can also contain “payloads” that damage host computers. Payloads are pieces of code written to perform actions on affected computers beyond simply spreading the worm. Payloads are commonly designed to steal data or delete files. Some payloads even create backdoors in host computers that allow them to be controlled by other computers. Malicious parties can use networks of these infected computers (“botnets”) to spread spam and perform denial-of-service attacks. (8 worm Tools are available.)
8. APK File crypter and Binders Tools
Thus, a crypter is a program that allow users to crypt the source code of their program to Bypass antivirus detection..
9. File Extension Spoofers Tools
extension spoofer that will change your dangerous file (not only) into something like “Presentation-for_schoolexe.pptx”, “exeexeexe.txt”, “notepadbat.jpg” without “.exe”, “.bat”, “.cmd” etc. at the end. (10 Extension Spoofers Tools are available.)
10. Proxy Tools
A proxy server is basically another computer which serves as a hub through which internet requests are processed. By connecting through one of these servers, your computer sends your requests to the server which then processes your request and returns what you were wanting. | Jdsingh Hacker Tool Kit
11. EXE File Binders Tools
File binders are utility software that allow a user to “bind” multiple files together resulting in a single executable. They are commonly used by hackers to insert other programs such as Trojan horses into otherwise harmless files, making them more difficult to detect.
20 plus exe binders are available in jdsingh hacker tool kit.
12. Others Tools
1.Advance Deface Creator
2. Black File Pumper
3. Tartou2 File Pumper etc tools are available
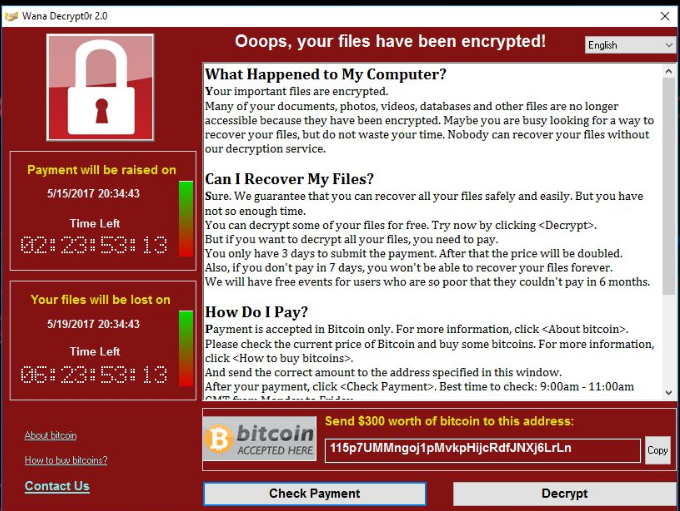
13. Ransomwares Pack Downloader Tools
Ransomware is a form of malware that encrypts a victim’s files. The attacker then demands a ransom from the victim to restore access to the data upon payment.
Users are shown instructions for how to pay a fee to get the decryption key. The costs can range from a few hundred dollars to thousands, payable to cyber criminals in Bitcoin.
Different types of Ransomware tools are available in jdsingh hacker tool kit. || hackers toolkit






Comments
Post a Comment