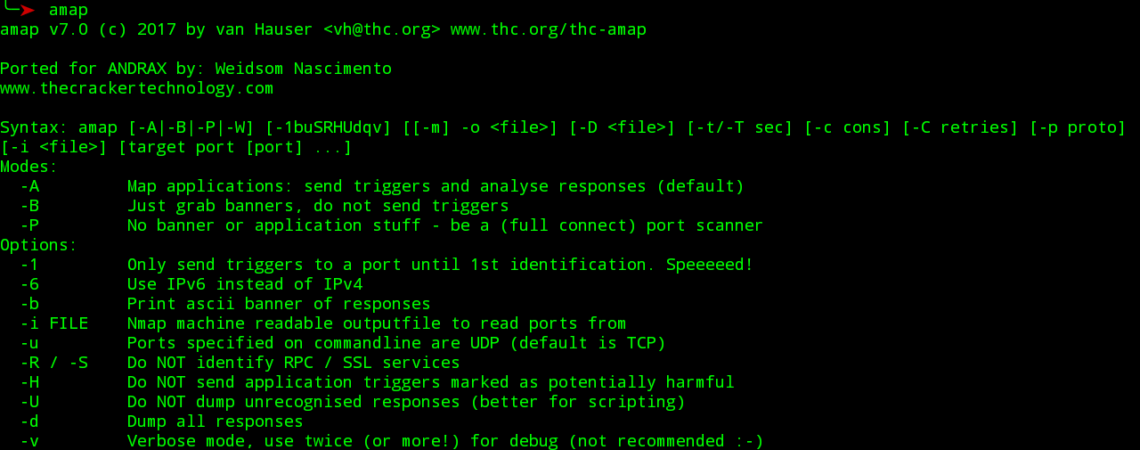
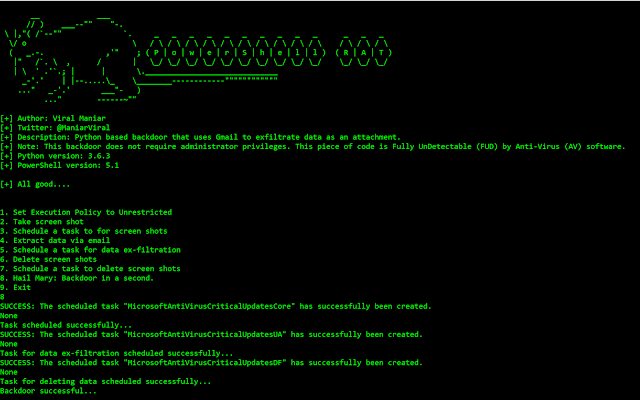
ace voip | Penetration Testing Tools
ACE (Automated Corporate Enumerator) is a simple yet powerful VoIP corporate directory enumeration tool that mimics the behavior of an IP phone to download name and extension entries that can display a given phone on its screen interface. In the Read more…