New best story on Hacker News: Tabler: Free and open source dashboard HTML/CSS framework
515 by jakearmitage | 85 comments on Hacker News.
New best story on Hacker News: US regulators will certify first small nuclear reactor design
538 by papa-whisky | 327 comments on Hacker News.
New best story on Hacker News: Google’s Nest will provide data to police without a warrant
508 by mikece | 393 comments on Hacker News.
New best story on Hacker News: Facebook's TikTok-like redesign marks sunset of social networking era
666 by jedwhite | 657 comments on Hacker News.
New best story on Hacker News: Tesla ransoms car owner remotely by cutting 1/3 of their range
750 by noasaservice | 517 comments on Hacker News.
New best story on Hacker News: Two weeks in, the Webb Space Telescope is reshaping astronomy
655 by theafh | 393 comments on Hacker News.
New best story on Hacker News: Amazon sales of Deep Learning with Python are counterfeit
591 by jmillikin | 179 comments on Hacker News.
New best story on Hacker News: Hertz paid Accenture $32M for a website that never went live (2019)
600 by sogen | 394 comments on Hacker News.
New best story on Hacker News: Potential fabrication in research threatens the amyloid theory of Alzheimer’s
575 by panabee | 234 comments on Hacker News.
New best story on Hacker News: Former Coinbase PM charged in cryptocurrency insider trading tipping scheme
686 by tempsy | 417 comments on Hacker News.
New best story on Hacker News: Cheap junk flooding Amazon has brand names like MOFFBUZW
831 by rafaelm | 391 comments on Hacker News.
New best story on Hacker News: Ask HN: What are some cool but obscure data structures you know about?
807 by Uptrenda | 386 comments on Hacker News.
I'm very interested in what types of interesting data structures are out there HN. Totally your preference. I'll start: bloom filters. Lets you test if a value is definitely NOT in a list of pre-stored values (or POSSIBLY in a list - with adjustable probability that influences storage of the values.) Good use-case: routing. Say you have a list of 1 million IPs that are black listed. A trivial algorithm would be to compare every element of the set with a given IP. The time complexity grows with the number of elements. Not so with a bloom filter! A bloom filter is one of the few data structures whose time complexity does not grow with the number of elements due to the 'keys' not needing to be stored ('search' and 'insert' is based on the number of hash functions.) Bonus section: Golomb Coded Sets are similar to bloom filters but the storage space is much smaller. Worse performance though.
New best story on Hacker News: Tell HN: You can't hire because you don't post salary ranges
756 by Carrok | 399 comments on Hacker News.
At the start of this year, Colorado has changed to require every job posted to list a salary range. Other states are also beginning to follow suit. I am currently job hunting. I started looking locally, everything lists salary ranges, perfect. I can know which positions to skip and which ones might be a good match right away. No need to waste time with 7 rounds of interviewing only to find out the salary is 50% of what I currently make. Now I've begun widening my search to remote work, as the idea of commuting to an office in 2022 is completely insane to me. Most jobs on nation-wide job boards do not post a salary range. I will not even click on those job postings. It's simply not worth it. Further, after seeing so many positions listed _with_ salary ranges, when I see one without a salary range it makes me feel like you have something to hide and are trying to trick me. So the next time your team starts discussing why you can't seem to hire, maybe ask if you are publicly posting salary ranges on these positions?
New best story on Hacker News: Flipper Zero – Portable Multi-Tool Device for Geeks
663 by clouddrover | 204 comments on Hacker News.
New best story on Hacker News: TeamViewer installs suspicious font only useful for web fingerprinting
634 by kevincox | 207 comments on Hacker News.
New best story on Hacker News: EU Digital Markets Act, aimed at Google, Apple, Amazon, approved
627 by Gareth321 | 742 comments on Hacker News.
New best story on Hacker News: FCC: TikTok is unacceptable security risk and should be removed from app stores
506 by scanr | 444 comments on Hacker News.
New best story on Hacker News: New documents reveal scale of US Government’s cell phone location data tracking
466 by DamnInteresting | 215 comments on Hacker News.
New best story on Hacker News: Blue Zones, where people reach age 100 at 10 times greater rates
444 by ivanvas | 256 comments on Hacker News.
New best story on Hacker News: Iceland’s forest and bush cover has increased sixfold since 1990
404 by toto444 | 260 comments on Hacker News.
New best story on Hacker News: Ask HN: I love programming but hate the industry. Can anyone relate?
384 by DanUKs | 293 comments on Hacker News.
I love building and working - always have, always will. I've been programming for nearly 10 years, 5 of those professionally but the industry is literally destroying my soul and it has recently become crippling. I've been in all kinds of jobs, from start-ups to massive corporate companies. I'm forever building my own side projects as I love it, as well as love the idea of making my own living but as you all know, side hustles don't make money over night. I'm currently in a great job. By great job I mean, the money is really good, there's room to grow and the opportunities are endless... Yet I can't bare it. I can't bare the devs that go out of their way to work weekends without being asked, I can't bare the endless meetings, constant micromanagement, bringing the stress home to my family. I don't know where or who to turn to. Can anyone relate?
New best story on Hacker News: Tell HN: Internet Archive is facing a Big 4 Publishers lawsuit
422 by antiverse | 119 comments on Hacker News.
Not sure why this isn't more prominently highlighted, but this is a very culturally significant project and a custodian of a tremendous amount of Internet and WWW-oriented history. I would imagine HN would put this at the forefront of the discussions happening here. I'm not affiliated, but I am a concerned netizen. All of us here have benefited from The IA. Please help raise awareness as to what is happening. Read more here, and elsewhere - https://ift.tt/3h1MLvR > In June 2020, four major publishers—John Wiley & Sons and three of the big five US publishers, Hachette Book Group, HarperCollins and Penguin Random House—filed a lawsuit against the Internet Archive, claiming the non-profit organization, “is engaged in willful mass copyright infringement.” > The lawsuit stems from the corporate publishers response to an innovative temporary initiative launched by the Internet Archive during the first months of the coronavirus pandemic called the National Emergency Library. Given the impact of the public health emergency, the Internet Archive decided to ease its book lending restrictions and allow multiple people to check out the same digital copy of a book at once. > Up to that point, the Internet Archive had established a practice of purchasing copies of printed books, digitizing them and lending them to borrowers one at a time. When it kicked-off the emergency lending program, the Internet Archive made it clear that this policy would be in effect until the end of the pandemic. Furthermore, the archive’s publishers said that this program was in response to library doors being closed to the public during the pandemic. Under conditions where the Internet Archive was the only means of access to titles for many people, the policy was justified and a creative response to COVID-19.
New best story on Hacker News: Unity is acquiring a company who made a malware installer
434 by doener | 123 comments on Hacker News.
New best story on Hacker News: Show HN: I built an app for when I talk too much in online meetings
432 by interleave | 189 comments on Hacker News.
Hey HN! Alexis here, I’m a product manager and software developer in Berlin by way of New York. I want to show you this app I made – It’s like a "buddy" for those, like myself, who inadvertedly talk too much in meetings. The app gives me feedback and a little more in control of what I have influence over by: * Keeping track of how long I’ve been speaking * Catching myself before I talk too much * Developing a better sense of timing I truly love having conversations with people in real-life. But online meetings, especially group calls, tend to make me nervous. I can't read body language. The tone of voice, micro-experessions and social cues get lost. If you, too, accidentally talk too much too often, check it out "Unblah". Watch the quick 2-minute demo and download the macOS app over at https://unblah.me/ . Cheers! Alexis PS: There’s a whole FAQ section for common questions you may have – Including if this is yet another "native" Electron app ;) edit: bullet-list formatting
New best story on Hacker News: Woman ‘dehumanised’ by viral TikTok filmed without her consent
692 by phs318u | 601 comments on Hacker News.
Anonymous Leaked a Bunch of Data From a Right-Wing Web Host
The hacktivist collective targeted the domain registrar Epik for providing services to clients including the Texas GOP, Parler, and 8chan.
HACKTIVIST COLLECTIVE ANONYMOUS claims to have obtained gigabytes of data from Epik, which provides domain name, hosting, and DNS services for a variety of clients. These include the Texas GOP, Gab, Parler, and 8chan, among other right-wing sites. The stolen data has been released as a torrent. The hacktivist collective says that the data set, which is over 180 GB in size, contains a "decade's worth of data from the company."
Anonymous says the data set is "all that's needed to trace actual ownership and management of the fascist side of the Internet that has eluded researchers, activists, and, well, just about everybody." If this information is correct, Epik's customers' data and identities could now fall into the hands of activists, researchers, and just about anyone curious enough to take a peek.
Epik is a domain registrar and web services provider known to serve right-wing clients, some of which have been turned down by more mainstream IT providers due to the objectionable and sometimes illicit content hosted by the clients.
Anonymous' activities began with what the group calls "Operation Jane" after the Texas Heartbeat Act was signed into law this month. The restrictive abortion law allows private individuals, not necessarily government bodies or the police, to enforce the six-week abortion ban. According to the act, any Texas resident can bring a civil lawsuit against any person who performs or helps to facilitate an illegal abortion—and claim at least $10,000 in damages.
A note announcing the hack was spotted by journalist Steven Monacelli, who has since been doxxed by an Epik supporter.
Among the data set are various SQL databases containing what appear to be customer records associated with every domain name hosted by Epik. Ars analyzed a small subset of the leaked data set, including what a source calls an Epik employee's mailbox, which contains correspondence from Epik CEO Rob Monster.
Members of the whistleblower site Distributed Denial of Secrets (DDoSecrets) have also made the data set available via alternate means for those unable to use torrents.
"We are not aware of any breach. We take the security of our clients' data extremely seriously, and we are investigating the allegation," an Epik representative told Ars.
Anonymous also tampered with Epik's knowledge base to mock the company's denial of the breach.
"On September 13, 2021, a group of kids calling themselves 'Anonymous', whom we’ve never heard of, said they manage[d] to get a hold of, well, honestly, all our data, and then released it," said the altered knowledge base, as seen in an archived copy. "They claim it included all the user data. All of it. All usernames, passwords, e-mails, support queries, breaching all anonymization service[s] we have. Of course it’s not true. We’re not so stupid we'd allow that to happen."
The knowledge-base page ends by sarcastically saying, "We did write this ourselves, this is obviously not part of the hacked account." Epik has since removed the page.
Prior to this incident, Anonymous defaced the Texas GOP website by replacing references to "Help Texas Stay Red" with "Texas: Taking Voices from Women to promote theocratic erosion of church/state barriers." The group also added "donate" links to reproductive health care nonprofit Planned Parenthood.
New best story on Hacker News: Amazon admits giving police Ring camera footage without consent
776 by Pakdef | 459 comments on Hacker News.
New best story on Hacker News: James Webb first images – complete set of high resolution shots now live
810 by crhulls | 318 comments on Hacker News.
How To Hack Instagram Account In 2022 || All Methods
For whatever reason, there are always people who want to hack social media accounts. || Hack Instagram Account
Instagram is one of the most popular social media in the world. If you are looking for hacking methods for Instagram then you are on the right page.
- How to Hack WhatsApp Account
- HACK INSTAGRAM ACCOUNT 2021
- How To Get Free Instagram Followers
- Facebook Hacking Tricks 2021 | Faceboohack
- Hack Instagram Account Using BruteForce 2020
- New WhatsApp Bugs Could’ve Let Attackers Hack Your Phone Remotely
- Hack Instagram : Track Unfollowers, Increase Your Followers, Download Stories
But before I share working methods I want to discuss website claiming they can hack any account within seconds.
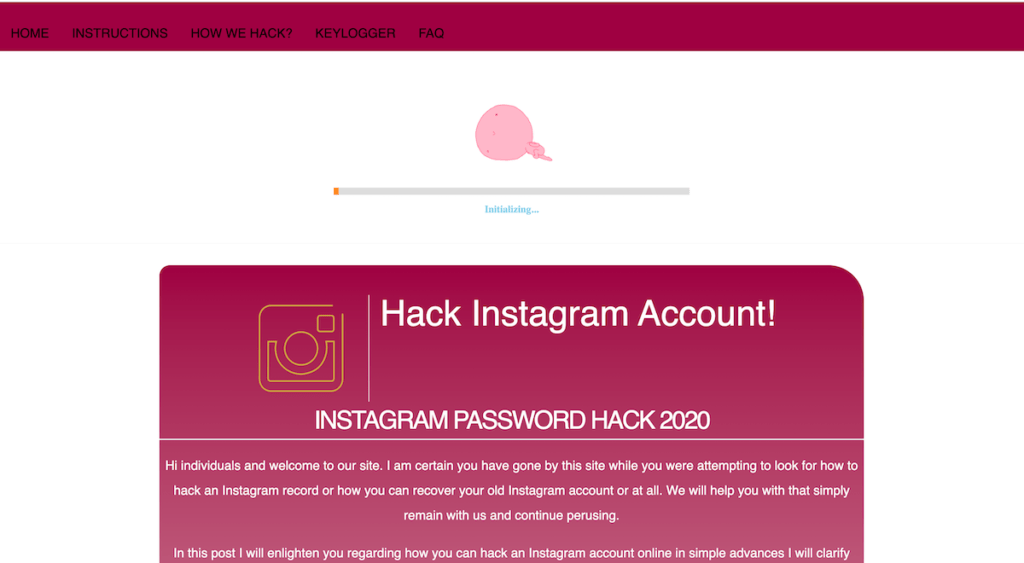
These type of websites doesn’t work. In the end, you have to complete a survey, where you will get nothing.
Instagram puts billions of dollars on security these simply can’t hack within seconds.
How To Hack Instagram Account
The only way to hack any account is to make your victim fool with some technical skills.
For example, providing them a fake login page that will look like a real Instagram login page. On login, you will receive the password & the victim will redirect to the original website.
These are the working methods to hack Instagram
- Keylogger
- Phishing Attack
- How To Create Phishing Page
- Firebase Accontbot Setup
- Changing Code
- Uploading
- How To Create Phishing Page
- Social Engineering
- By Hacking Facebook Account
- By Creating Fake Login App
- Wrapping It
Keylogger
This is the most underrated method to hack accounts. Basically, a keylogger is a software or app for smartphones that can record every typed word by the victim.
The biggest problem is you have to install a keylogger on the victim device.
On the internet, you can find both free and paid keyloggers. If you are looking for a free keylogger then try Smart Keylogger.
Here are the list of other keylogger apps. Keep in mind, you have to access the device again to view the data.
There are paid keyloggers available in the market. Once you install them on the victim’s phone you can receive all typed keyword data on your smartphone or any other device.
However watch is one of these kind of keylogger that you can try.
It is available for mac/windows & android phones. I tried on an android phone, it is undetectable.
But the installation part is complicated especially if you are a non-techy person. Here is a step by step article about how to install hoverwatch on an android smartphone.
How to Protect
- Computer users always keep machine up to date.
- Apply step 2 verfication on your accounts
Phishing Attack
In the phishing method, you create a website that looks similar to the original Instagram website. However when victims login with their username & password. He will be redirected to the original site and you will receive login details. Check the following screenshot.
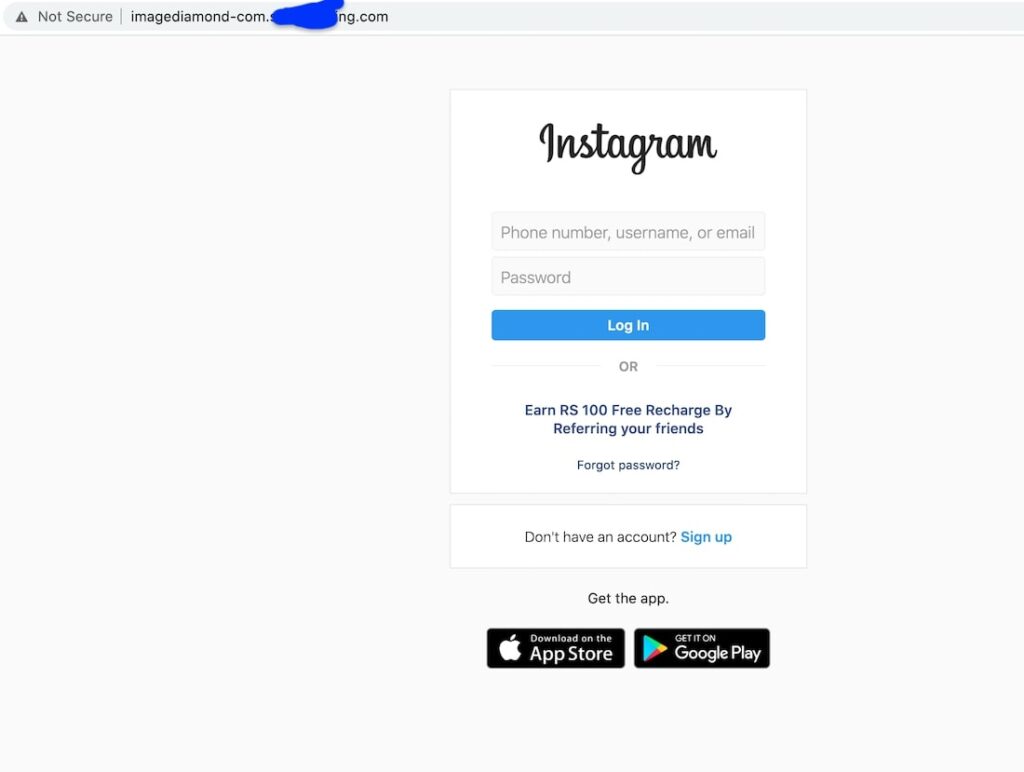
As you can see in the URL it is different than Instagram. Now don’t worry if you don’t know programming, I will show you step by step tutorial on how to create phishing page. || Hack Instagram Account
How To Create Phishing Page
Creating a phishing page is easy. But making an undetectable page is difficult. Free hosting continuously banning phishing websites, Browser also starts warning the users.
But still, even after these hurdles, you can create working phishing. In fact, I did it, It will just take some extra work. Here are the things that you need to create an Instagram phishing page.
- Phishing script: Download Here
- Firebase Account: Create a Firebase account & Setup a Project as well, Learn here
- Free Hosting: Sign Up for 000webhost.
Here are the steps that you need following after doing above three things.
Firebase Accontbot Setup
- First of all, you need to create a firebase account. This is where the username & password will be saved. Visit firebase.google.com on your phone. It will show you something similar to the following page. Click on get started button.
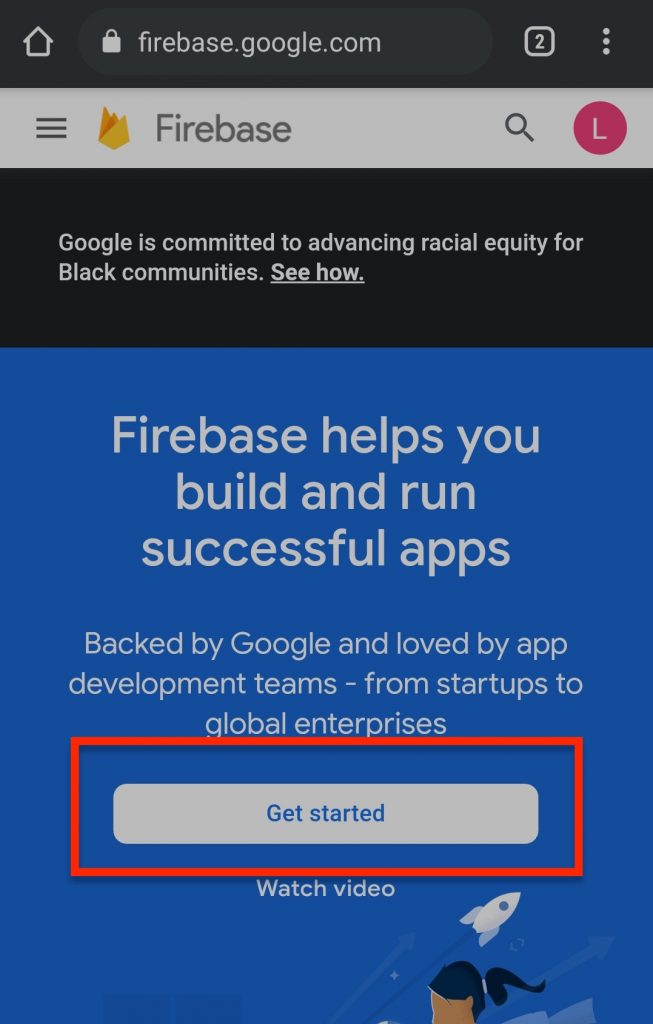
It will open a new page where again you need to click on the create project.
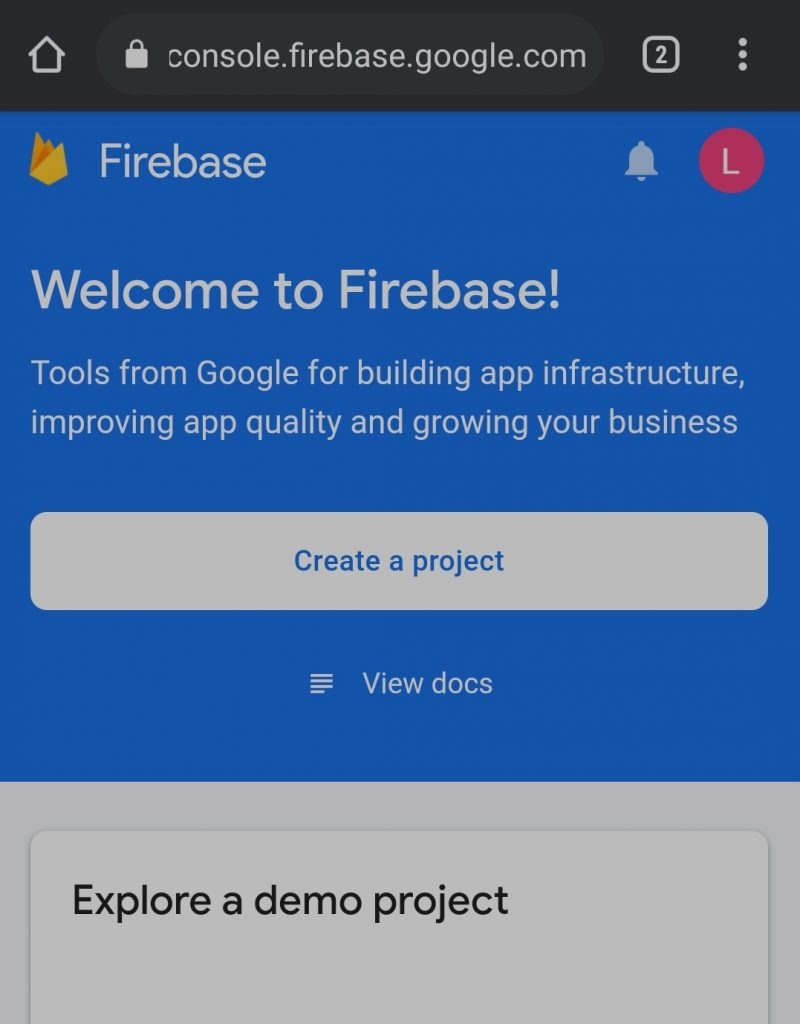
- Type your project name (type anything it doesn’t matter) and click on the continue button.
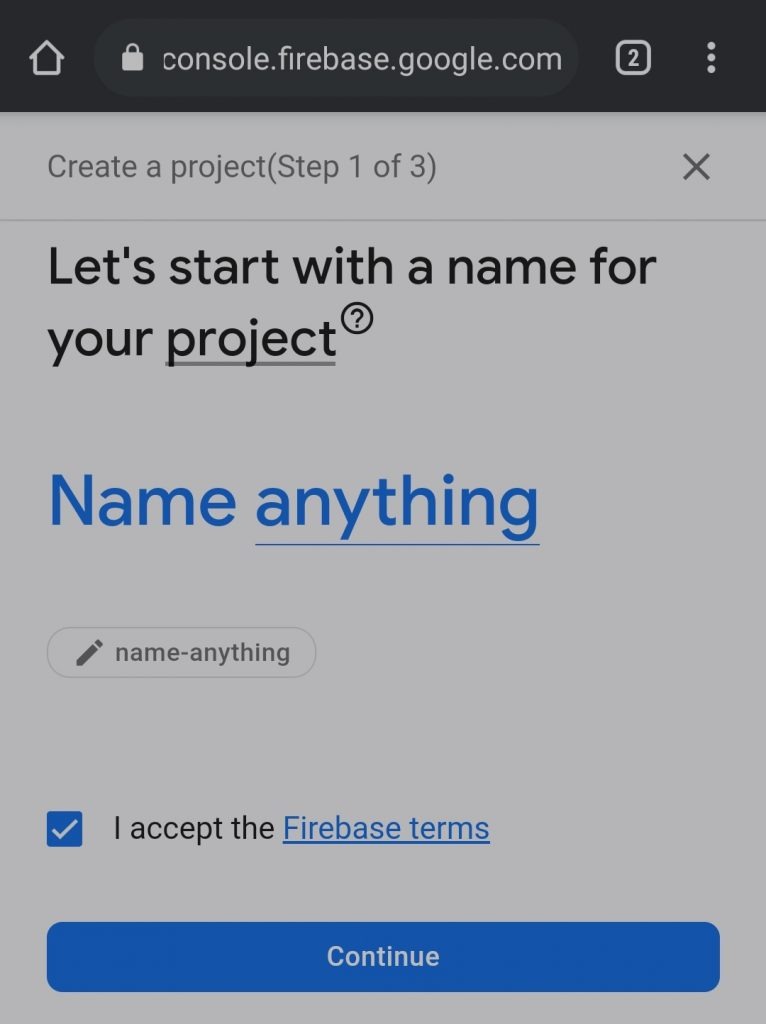
- On the next page, turn off the Google analytics report and click Create Project button.
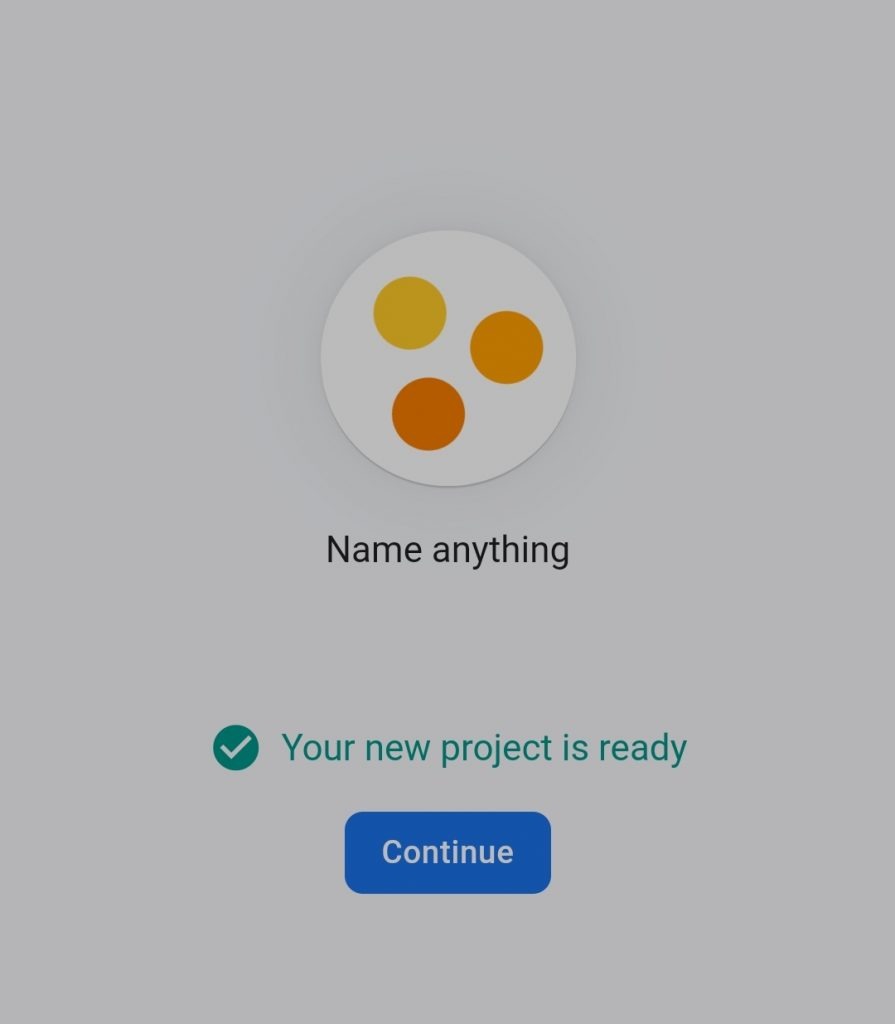
- It will start creating your project, once done you will see something similar to the following page. Here click on the continue button. || Hack Instagram Account
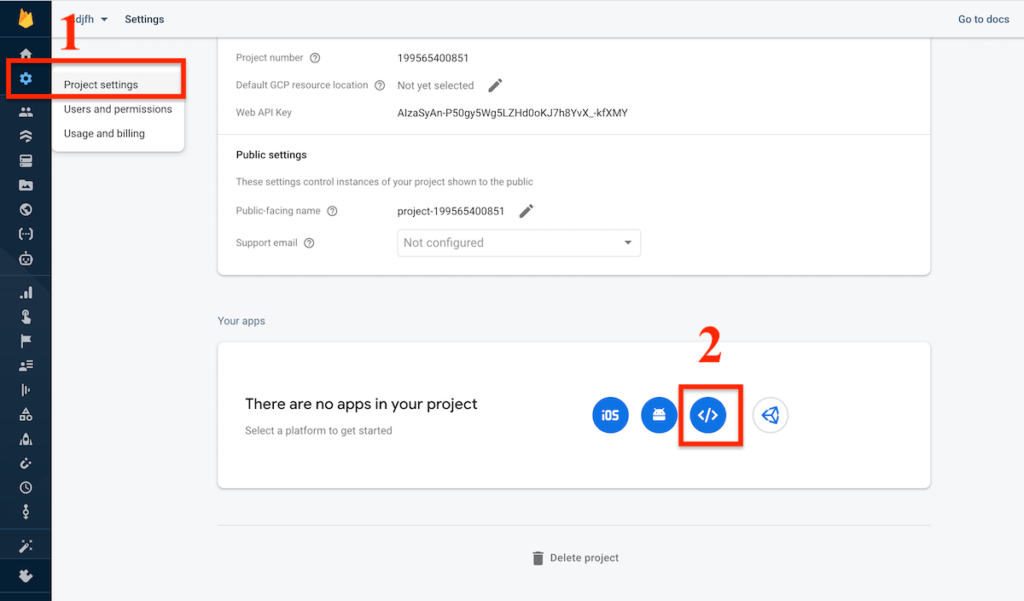
- On the next page, You will see the Dashboard of the firebase project. Click on the gear icon and then select Project settings.
- After that click the request desktop site from the 3 dot menu. It will show you something similar to the following page. You need to click on the Code icon as shown in the screenshot.
- This will take you to a new window where you need to type the app name. On Clicking Register Button, will show you a firebase code. || Hack Instagram Account
- As shown in the screenshot, copy the code starting from var= to (firebaseConfig);
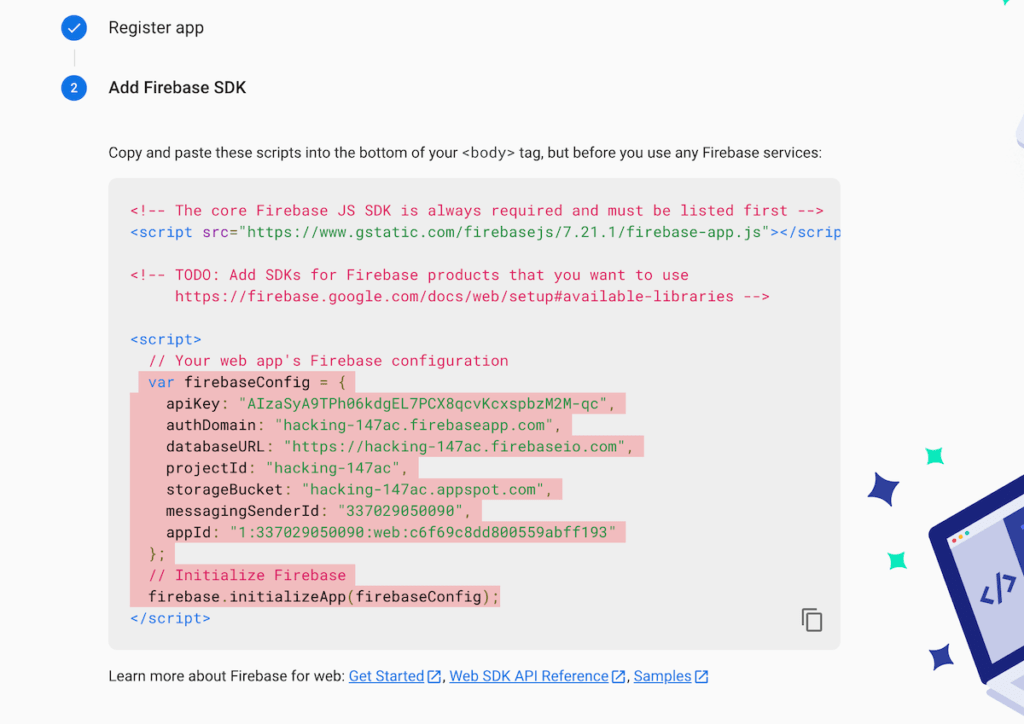
- Save these Codes In the notes app you need it later on.
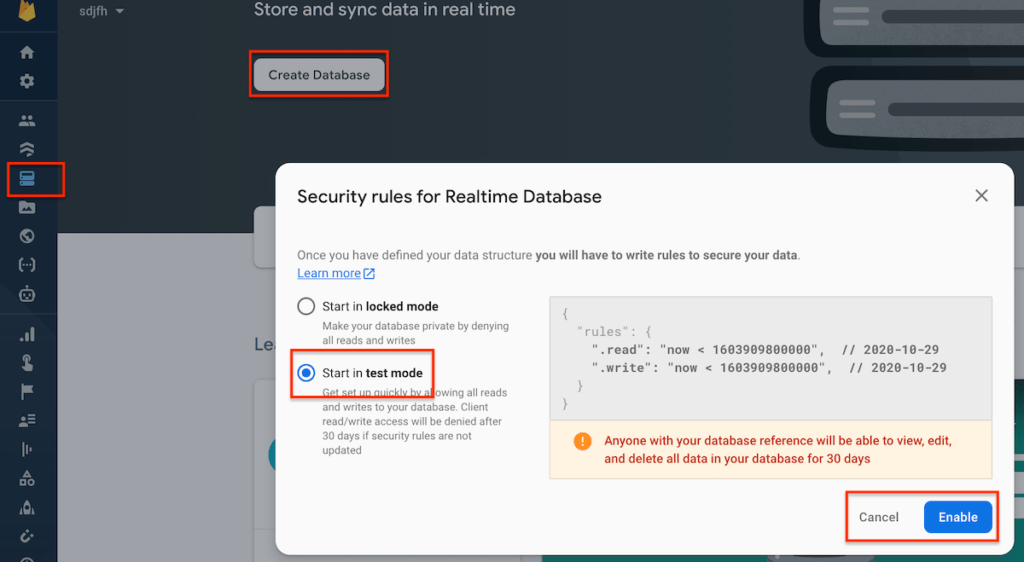
- Here in the firebase click on go to console button then Chose the Real-Time database from the left sidebar. Then click on the Create Database button. You’ll be prompted to choose a test or locked Mode. Select the test code and click on Enable button.
- Now Go to Rules & Change both read & write to true
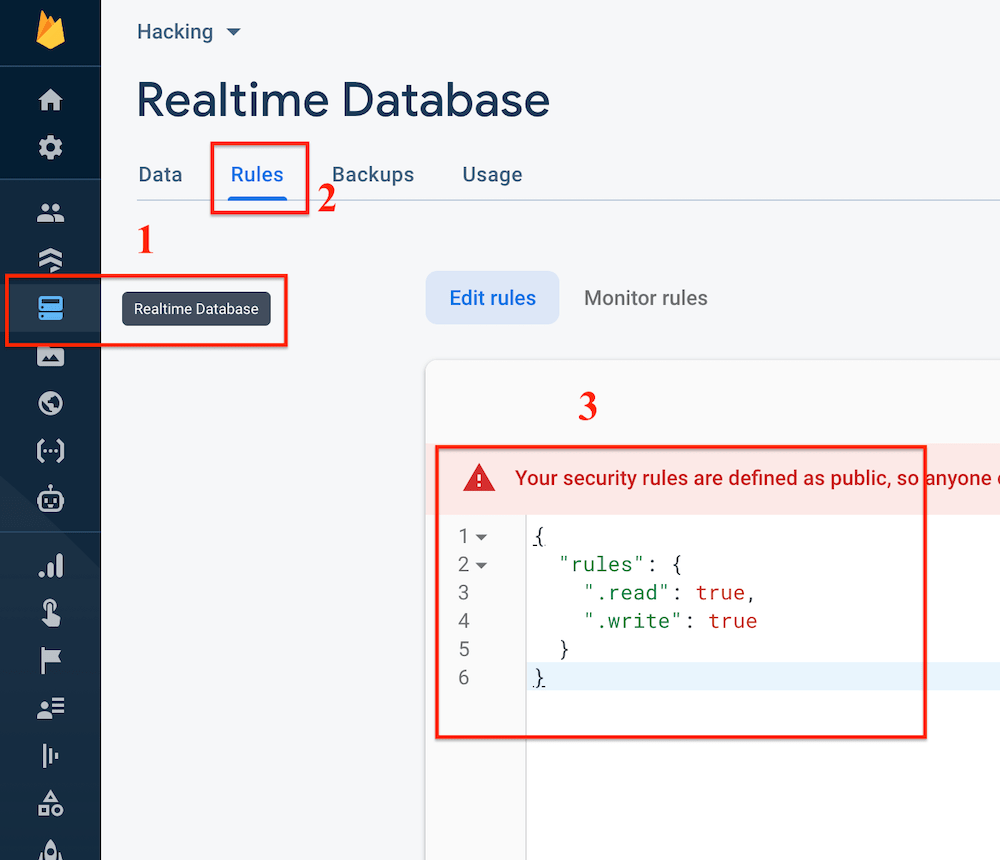
Changing Code
- I assume you have download the phishing script. If you haven’t here the link once again. This script is in a zip folder when you tap on it, it will show you the extract option. Make you extract it.
- You will get 3 things, the first one is the index.htm file & the 2 folders. Now Open the index.htm using any text editor such as notepad. Android users can use the HTML Editor.
- Scroll Down until you did not find firebase settings as shown in the screenshot. If you are an android user and using the above app then you will find code in the 459 line as shown in the screenshot. ||
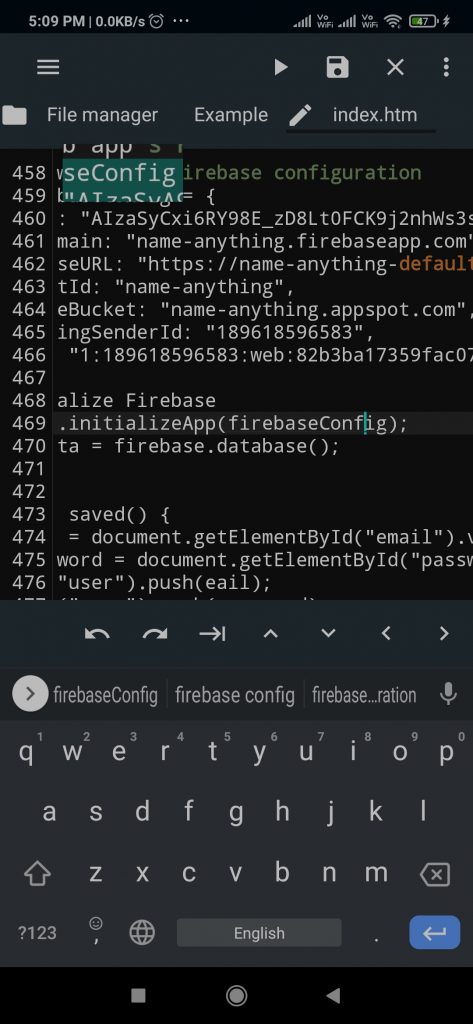
- Change these codes that you have copied in the 8th step of Firebase Settings
- Save the File
- Go back to file manager and select all extracted items (index.html file and 2 folders) then compress as shown in the screenshot.
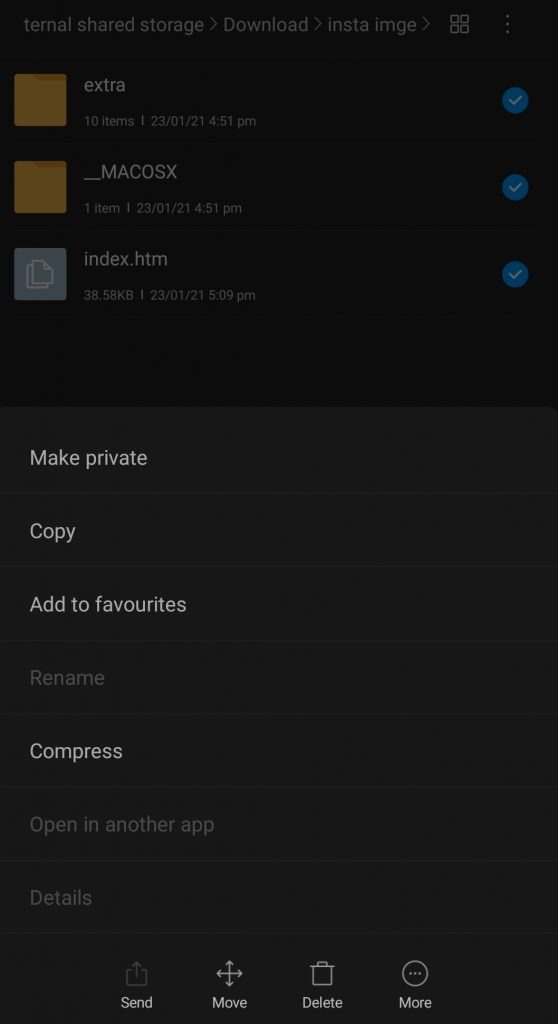
Uploading
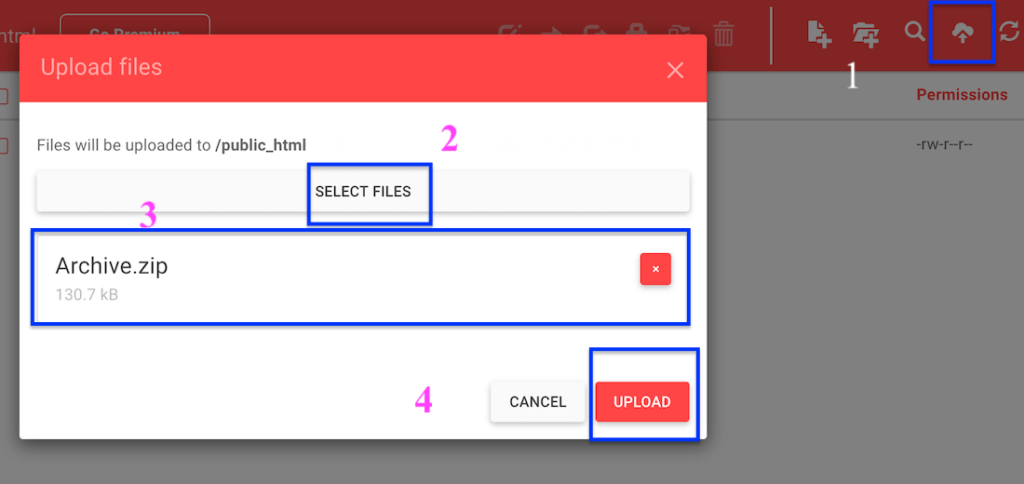
- Now login to your 000webhosting account. After that find the File Manager.
- Open it & go to public_html folder. Upload the Zip Folder. The following screenshot describes how to upload a zip folder
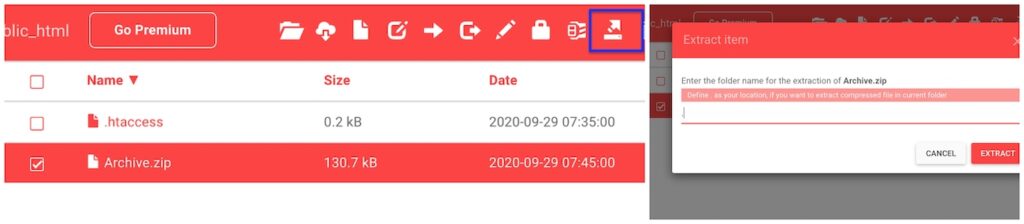
- After uploading, Select the file and select the Extract icon. It will prompt you to the location. Type . (Dot)
- Now Go back to My Sites, open site URL. It will show you something like this
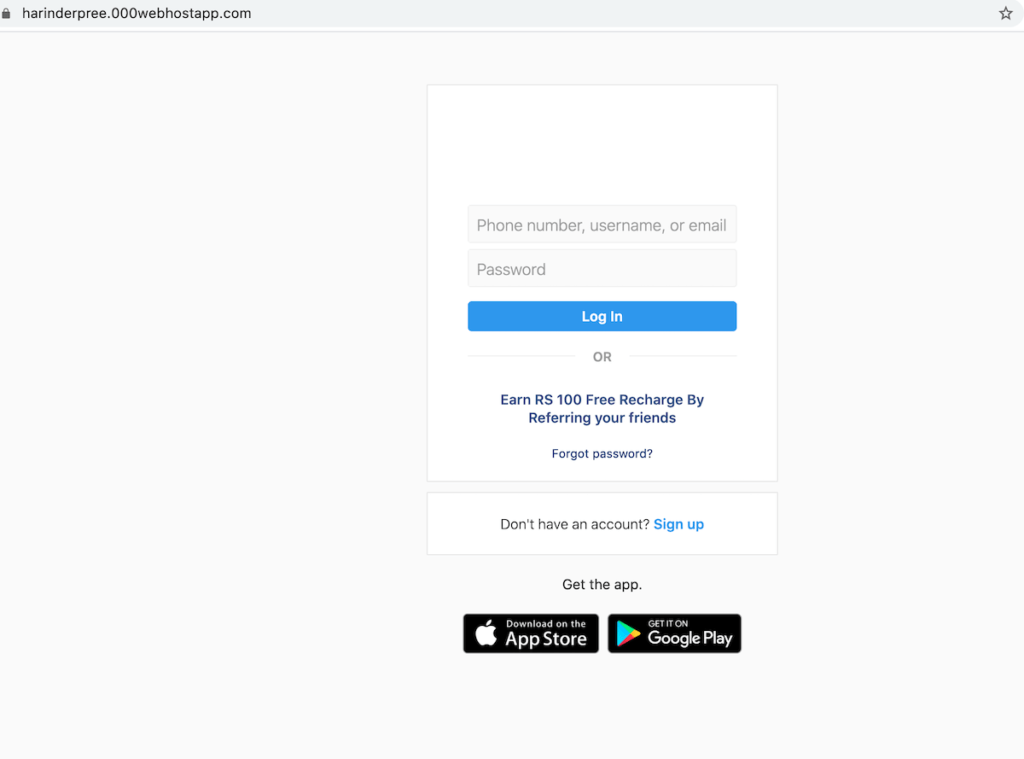
- Login with any account to check your account.
In the Firebase→Realtime Database, you will get your login details as you can see in the screenshot.
If you didn’t receive anything probably you haven’t change the code successfully. || Hack Instagram Account
Creating a phishing page is a different thing but the convincing victim is totally different concept. On this page, I write down Earn RS 100 as you can see in the screenshot. So you can use say something like I will get free recharge. || Hack Instagram Account
How to Protect yourself
- Always check URL before login
- Do not Open Any link from unknown source
Social Engineering
Social Engineering nothing just guess the password. But the above methods you can also social engineering. To Convince victim for login into the fake page, installing a keylogger, etc.
A lot of people set a password use the name of dad/mom with a mixture of some other characters.
Some people use the same password for every account. So if you can get password of other account then you might get their instagram account.
How to Protect your account
Use a Strong Password. Here is my recipe to create a strong password. Think about a sentence in mind, anything. For this example let’s use the following one.
Tinku was Our First Dog.
Now Pick first character of every word. It will look something like this
Twofd
Last but least add some special characters to it.
Two)(*fd
I have picked 098 special characters so I can remember. Now you have a strong password.
By Hacking Facebook Account
A lot of people use login with facebook to access instagram account.
You can use the above mentioned methods to hack fb account.
Before you send the Instagram phishing page make sure you find out how your victim access Instagram account.
By Creating Fake Login App
A lot of users browse insta by the android app. If you have app development knowledge then you can use create a fake Instagram app.
Here I what I did to hack account.
- Get phone to browse Instagram
- Uninstall original app
- Installed Fake App
In the fake app when my victim tried to login into his account. App Show an error
Something is wrong, Please uninstall current version & install latest version from play store.
In the backend, it forward me his username & password. To create fake either you can spend 2-3 months in app development or hire a app developer from fiverr.
How to Protect yourself
- Apply step-2 verification on your account
Wrapping It
No matter how secure the internet become there will be always some ways to hack it.
If you have any question/query or feedback let us know by the comment section. rat 888 free Download
How to use an Instagram account hacker in 2021
Social media plays a major role in this technical world. One such popular social media is Instagram. Instagram provides a huge digital platform for all kinds of people to share their thoughts, ideas, videos, and photos to their nearer and far people. Instagram just requires an email id and a strong password to access the Instagram account. It makes the people’s life easier to access freely and to celebrate their life. virtual times revolutionized times muthiyah instant risk
Instagram passwords are unique for an individual. Every password will be different for the account holders. It is not easy for others to get into your account to access your pages. Do you wonder what will you do when your account gets locked or unfortunately you forgot the password or when you lost the phone? Sometimes you need to access your kids or spouse account, whatever be the reason, when there is no chance of access your profile without the account details like username or password what will you do? limited banking ips
Here are some tips to hack the Instagram account thereby helping you to access your profile most importantly without your login information. offer days
The content disclosed here is to be used ethically. We are strongly against the misuse of information and gaining unauthorized access to the account. It is illegal to access the information of other people‘s accounts using the content posted in this article.
Reasons you might wan tto hack an Instagram account
Hacking the Instagram account should have a valid reason like for your use when you cannot access your profile or at the time of requisition from the other person to break into their profile. Other than gaining access to other accounts are meant to be an illegal and unethical way of hacking. knowing physical
US Federal government proposed a strict order for the people who are breaching the ethical hacking rules. If there is any proscribed shown, then it leads to sentence or penalty depending on the issue thrown by the person.
The top 3 ways to hack an Instagram account
Let’s get into the top 3 methods to hacking the Instagram password which are the working methods of 2021.
Brute forcing attack
- The brute force method is often used to hack the account. It involves trial and error based hacking. It is a simpler method to get the right information of account users. It is a very effective method as it collects data from the ads posted in your profile or using malware to hack the account. The brute force method is also depending on how strong the password created by the user.
- There is multiple brute force app available online which supports you to gain the access of your profile or requested profile. Some of them are:
- InstaPwn: The website enables the user to use the service on the go. It automatically updates the password combinations and also helps the users to back up their photos and videos safely and securely. It also cleans your browser from cookies.
- InstaEntry: The website is specially designed software for the Instagram app. It has an upgraded algorithm that provides greater support to crack the password running through all sorts of combinations.
- InstaRipper: The app can be downloaded from the play store. It is a user-friendly app. You just enter the id which you need to crack; the app will automatically start booting for the combination of passwords.
Phishing the account credentials
- The phishing page is one of the oldest methods of cracking passwords. It is also a popular working method that helps to create a fake login page of Instagram, thereby getting the information from the account holder directly using their email id. This page can be used by whosoever wants to use the account. It works like the user will receive an email saying “change password” and by then the user fills in the details which enable the hacker to get the information of the instagramer easily.
- Another phishing page method is that creating a fake third party application through which the hacking happens by asking the account holder to manage the accounts. So, to use this method, it is enough to have little knowledge for the hacker to crack the password by creating a phishing page with a web host account. It is the cheapest method of hacking.
Social engineering / guessing the password
- The next hacking method is social engineering. It is one of the direct hacking techniques to crack the password. If the user is a known person of the hacker then, the hacker could use a direct guessing the password method like name of the favorite person, pet name, house number, birth date, and other possibilities to hack the password of the account holder. methods
The other methods of hacking the Instagram passwords are: target
- Rainbow table attack: Here the hackers collect all the possible password combinations in the form of hash. Now their work is to compare the targeted password with the collected hashed passwords. keylogger
- Keyloggers: It is one of the oldest hacking techniques to crack passwords. Here the hackers record the keystrokes used by the user and are sent back to the third party, from there the hackers easily guess the password. code
Wrapping it all up
There are numerous hacking tools available over the internet. It is very easy for hackers to crack passwords with advanced technologies. The only thing you need to consider is the right techniques and information about the account holder. This ease the work of the hacker but it should be of ethical purpose. Illegal hacking will leads to stiff penalties and a jail sentence. eye
The account holder should be very careful in creating passwords. The hackers are left disappointed when the user uses a strong password which should not be guessed by others. With all mentioned above information about password hacking, the user should be aware of cyber security. They should be careful in disclosing personal information over the internet and also in the social media apps.
Top Instagram Hacks
By
Do you Want to Hack Instagram account / Instagram ID? Are you frustrated searching on the internet for How to hack Instagram ID and Password? Are You Searching For Instagram Hacker Tool 2020? Then you Have Came to Right Place, Here you Will Understand about Instagram Hacking, How to Hack Instagram Account and Passwords, and You will Also Get to Know About Instagram Hacker Tool. These Days Instagram Has Updated It’s Security Policies, But there are Still digit advent
When we think about IG Hacks we think it’s very difficult or it’s very easy doesn’t matter what you think. It is always very difficult and very easy to hacking account or any social media account means it depends on the account holder. space sending
Actually in this process doesn’t require a high level of hacking, you just need to follow the process of what we teach or tell you to hack Instagram account. We do not directly do Instagram hacking like a pro hacker but following things can help you to hack instagram account.
Many ways through which you can Easily Hack anyone’s Instagram ID and Password, So lets Discuss in brief about Instagram Hacking.
Instagram is one of the biggest Platforms for Photo And Video Sharing. Over 95 M Photos and Video are Shared on this platform every day. Many People had created their ID on Instagram and Share their Daily life photos and videos on it.
Also Read: How to Hack Facebook Account new technique and How to Hack Whatsapp
Table of Contents
Ways To Hack Instagram Account
Phishing for Instagram
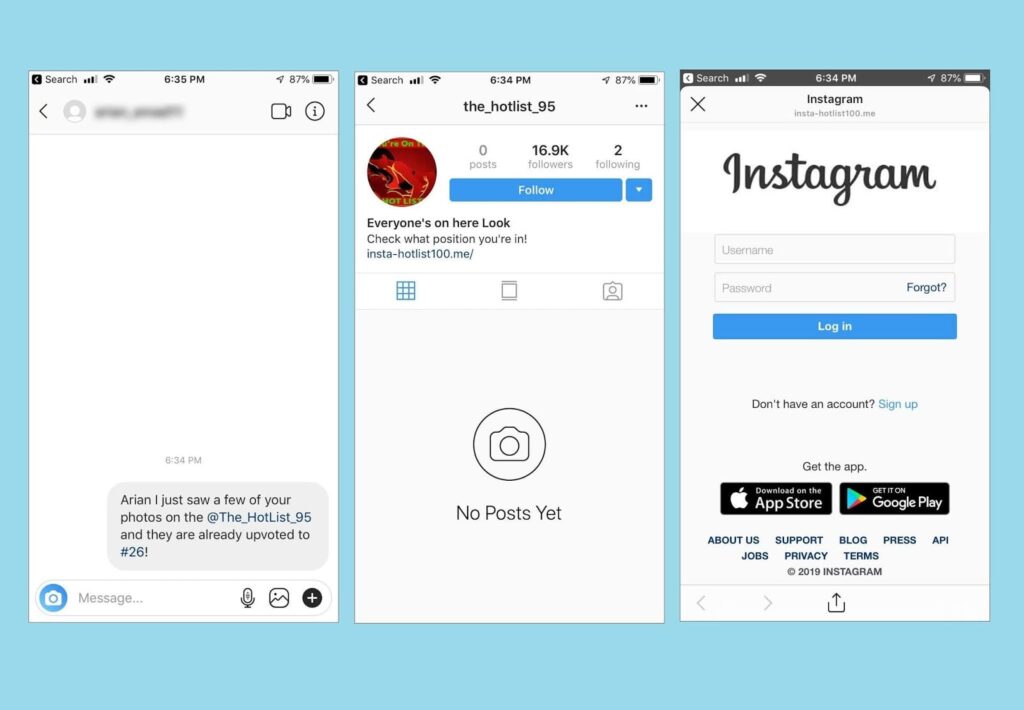
Phishing Is on the popular attack performed on every social media and daily thousands of Instagram Ids and accounts are hacked. The attacker uses a fake Clone web Page of Instagram login and sends it to the victim, as soon as victim login to Instagram gram thought that clone webPage attacker gets all his confidential information including Instagram Id and Instagram Password after that attacker Get full Access to than Instagram Account.
There are Several Ways to perform Phishing Attack to Hack Instagram Account
ShadowWave to Hack Instagram Account
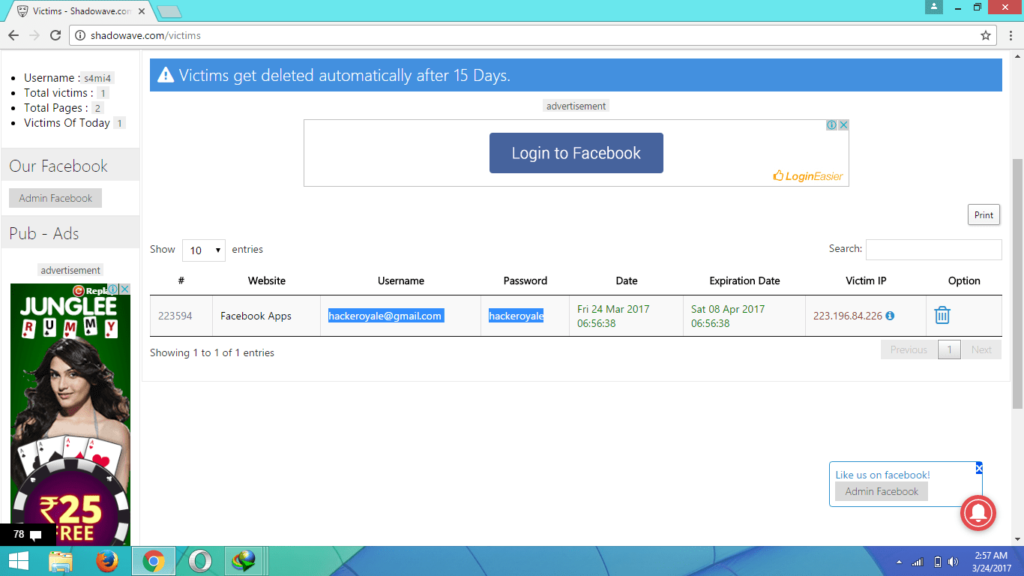
ShadowWave is a website Which provides you Prebuild Phishing Page for Instagram, Facebook, Twitter, and many other social media Network. This website Was created in 2014 in order to give the prebuild phishing page of Social Network. ShadowWave made Facebook hacking very easy and now It’s time to hack Instagram account.
Follow the process to create a Phishing page for Instagram on ShadowWave.
- Register on ShadowWave
- Select Instagram in Order to create Phishing Page
- Full fill the Requirements for a fake profile
- Accept all the Terms and Conditions
- Create the Page
- Copy the link URL and send it to Victim
Now, here Comes the Role of Social Engineering. You have to convince the victim anyhow to click on that link in order to fill up the Instagram Login Page. AS soon he submits his Instagram login ID and Password You will get his ID and Password in Victim Section on ShadowWave.
Also Read: How to Get Verified Badge On Instagram
Linux Tools to Hack Instagram Account
Kali Linux and Parrot OS are widely used operating systems by Hackers and they even come with many Prebuild tools for hacking. There are many numbers of Phishing tools available on the internet. These tools use your own system as a server to store Instagram Id and Password. The Phishing Link Generated by these tools only works until your terminal is open If you close your terminal Your stored Id and Password may be lost. You can download these tools Easly from Github and follow the installation process given at the bottom of the tool Description. These tools are mainly based on Python language. The list of Github Phissing tolls is given below.
- Hidden Eye
- Social fish
- Shellfish
- Spearfish
- Black Eye
Man in the Middle Attack (MITM) to Hack Instagram Account
Man in the Middle attack is one of the attacks commonly used by every Hacker. You can use MITM in order to Hack Instagram Account and collect ID and Password of Instagram User.
To do this attack Attackers and Instagram User Should have to be in the same network. Now as both Attacker and Instagram victim is connected to the same network, the Attacker will start scanning the network. An attacker can use many tools like arp Poisoning or Can Run Wireshark tool in order to capture the Packet.
This attack can also be done by creating Fake clone wifi as of original. AS the user comes to login to wifi his/her all traffic will be redirected from attacker fake access point. For Example: if A user login Instagram through ID and Password, the Attacker will get the full list of id and Password Easily. Listed Below a video will easily let you understand about MITM Instagram.
Hacking Instagram with SPY Tools
There are different spy tools also available on Internet that we can use to hack instagram account and password. These tools are most often use for both social site hacking as well for phone and PC hacking as well. By using the Spy tools, the hacker actually install the spyware tool in the victim’s phone and thus can gain the access of each and every activity of the victim. If you too would like to use the spy tools to hack the instagram account, than you too can choose different spy tools available on the internet. Here in this article also, we are also discussing below some of the popular spy tools that you can use.
Also Read: How to Hack Wifi and PUBG Mobile Hack
Hacking Instagram Account using Xnspy

XNSPY is one of the popular tools that most of the hackers are using to spy android phone. This tool has specific in-built spy instagram tool as well which is quite useful for instagram hacking. Different users are also using this tool for monitoring their instagram account as well. The tool is also useful to monitor the activities of your children or even of your employees. You can get complete access of the victim’s mobile phone using this spy tool such as photos, messages, instagram app etc.
Also Read: How to View Expired Stories on Instagram
Different Steps Involved to Hack Instagram Account with XNSPY
Step 1 – First, you need to subscribe with XNSPY tool on your device as well on the victim’s device also.
Step 2 – If you are an Apple user, you can configure iCloud backup.
Step 3 – Now, you need to wait for 48 hours to properly configure the app. After the configuration, you can transfer the data from the target device to your own XNSPY dashboard.
Step 4 – To get the information about the target device, you need to login to your XNSPY account.
Step 5 – Go to Dashboard.
Step 6 – Visit “Photos.”
Step 7 – Click “search.”
Step 8 – Select “Instagram”
Step 9 – Select timeframe – ‘Today,’ ‘This Month,’ ‘This year’ or ‘All.’
Step 10 – Click “search.”
XNSPY is quite fruitful app and even the parents can watch their kids for all their social activities.
How to Hack Instagram Account using Spyhuman
Spyhuman tool is another effective tool for instagram hacking. As per one of the surveys, most of users on instagram are teenagers and they keep posting different photos, selfies or other sort of things such friend’s birthday, wedding party photos and so on. With the help of Spyhuman tool, you can easily access to all those photos of instagram of others. Apart from it, there are several other uses of spyhuman tool as follows:
- SMS and Whatsapp messages Tracking, GPS Tracking, Call recording, Social media accounts tracking and so on.
- You can access spyhuman from anywhere in the world online.
- It is compatible with android devices
- 24/7 Support.
How to Hack Instagram Account Using MSPY
If you don’t want to use the above spyware for Instagram account hacking then mspy would be one of the best alternatives available in the market this spyware has got many features as like other spyware. You just need to install this spyware on your victim’s phone and there you go. mspy will make Instagram much easier for you so if you don’t want to get into so much technical thing then you can choose mspy. There are some common features offered by MSP:-
- View all text messages (sent/received)Read all sent and received text messages sent in Instagram direct
- Look through shared links and textsView all links shared in Instagram direct messages
Hacking Instagram Account with Keyloggers
Keyloggers are one of the best tools often used by every hacker. These are software that is built in order to record keystrokes of PC / Laptop / Mobile. There are many keyloggers available in the market and you can easily use them in order to hack Instagram Account. Just install any of the keyloggers in your victim’s device and as soon as he gets logged in to his/ her Instagram account you will get the list of ID and Passwords. You can even use these keyloggers in order to get the list of Id and Password of other Social Media Networks. There are mainly two types of key Loggers:-
Software-Based Keylogger:- It’s a Computer Program which is made to monitor all of the keystrokes. It’s designed in a way, without the knowledge of your victim it is installed on your victim system and then you can monitor all the keystrokes. It is able to bypass small firewalls and antiviruses.
Also Read: Hiding Stuff behind another media :
Hardware-Based Keyloggers:- These key loggers are directly pluggen into Physical Devices Like CPU / Laptop which records Every Keystroke Ented By Victim including his/her Instagram Id and Passwords
Hacking Instagram by Social Engineering
Hacking Instagram Through Password guessing
Many people keep their Instagram password very simple and that can be guessed very easily. listed below are some of the common Instagram passwords.
- 123456
- 12345678
- Password
- 12345
- qwerty
- letmein
- 123456789
- Football
- 1234567
- Admin
- iloveyou
- monkey
- welcome
- abc123
- login
- 123123
- starwars
- passw0rd
- dragon
- hello
- master
- whatever
- freedom
- trustno1
- qazwsx
Hacking Instagram through Saved Passwords
This method will work only if you have a chance for physical access to targets smartphones. So what it is about?
Both iPhone and Android phone users have an option to save accounts passwords inside their phone to avoid typing them every time they want to login somewhere. In case they didn’t protect access to their stored passwords with their face/touch ID, you have a chance to see them! vulnerabilities
For iPhone, go to Settings > Passwords & Accounts > Website & App Passwords.
For Android users, go to Google Settings > Saved Passwords > click “Google Account” link > Now it will open Google Chrome browser with all saved passwords listed inside. vulnerabilities
To see saved passwords on a desktop browser is much easier than on mobile devices.
On Chrome, in an upper right corner click the three dots icon then Settings > Passwords.
On Mozilla Firefox, It’s the same icon location, click it then go to Logins and Passwords.
Conclusion
Don’t use this information to hack other users’ account under any circumstances. communication organization global
The United States legal system issues severe penalties for online fraud, and breaking into someone else’s Instagram account is precisely that – fraud, and identity theft. In essence, people who steal other users’ account access are copyright thieves that deserve punishment by the law. documents entertainment electronic screen
These technologies offer tremendous values to employers and parents, helping them secure people, assets, and family members. However, it may be tempting to be unethical in your use of the software. Before you decide to install any third-party software on the phones and devices of your family and employees, it’s important to think about the ethical and legal ramifications of your decision.
While it’s your prerogative on whether or not you install the software on your business assets, some employees may object to your actions as snooping on their behavior and an invasion of privacy. It’s essential to receive legal advice on the matter and ensure your employees have no recourse to sue you in the case that you discover any unauthorized communications or data transfer. calls cards cards
Parents can use these apps to keep tabs on their kids, but be careful of the consequences. It’s best to tell them outright that you’re installing these apps on their phone. If they discover you’re covertly spying on them, they may lose respect for you.
Categories
Popular Posts
-
How to Use WhatsApp Anonymously Without Original Contact

-
How to Crack Online Passwords with THC Hydra

-
Inshackle – Hack Instagram : Track Unfollowers, Increase Your Followers, Download Stories, Etc

-
New best story on Hacker News: EU citizens’ rights are under threat from anti-encryption proposals

-
(no title)

-
Powershell-RAT – Python Based Backdoor That Uses Gmail To Exfiltrate Data Through Attachment

-
Top 15 Security Utilities & Download Hacking Tools

-
New best story on Hacker News: Apple's Director of Machine Learning Resigns Due to Return to Office Work

-
How To Hack Instagram Account In 2022 || All Methods

-
New best story on Hacker News: PowerToys – open-source Windows utilities